Secure Cloud Management of Two-Factor Authentication for FortiGate | FortiToken Cloud
Many of today’s most damaging security breaches have been due to compromised user accounts and passwords. To address this, the adoption of a second factor in authentication has accelerated. Two-factor authentication, achieved through physical hardware or mobile application tokens, increases the certainty of the identity of users as they enter the network. FortiToken Cloud enables businesses of all sizes to manage their token implementations for FortiGate from anywhere there is an Internet connection. The service encompasses everything needed to implement two-factor authentication in your FortiGate environment including the FortiToken Mobile app with push technology, simplifying the end-user two-factor experience to a swipe or click to accept.
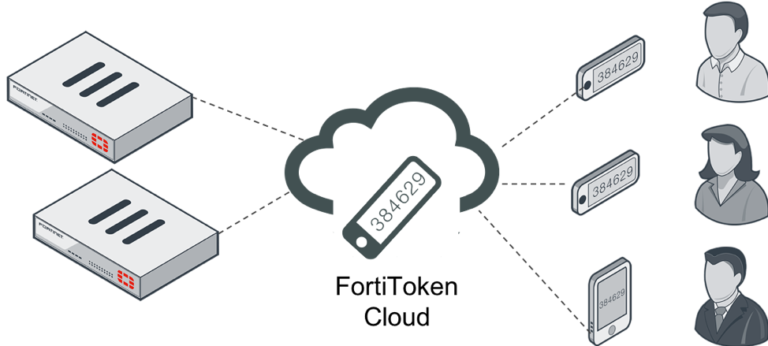
FortiToken Cloud offers centralized and simplified management of two-factor tokens in a FortiGate environment. From provisioning to revocation, FortiToken Cloud offers a robust platform to manage the lifecycle of your two-factor authentication environment. As a cloud service its intuitive dashboard is available anywhere there is an Internet connection. It’s a highly available platform equally able to scale to support organizations with a single FortiGate to managed service providers managing hundreds of FortiGates.
Centralized Two-Factor Management: supports the FortiGate environments of individual business and manage service providers.
.
Simplify deployment and administration of two-factor tokens Service includes everything necessary to implement two-factor authentication in a FortiGate environment including tokens via FortiToken Mobile
Easy deployment: no additional onsite hardware, software, or ACL changes
Stackable subscriptions: quickly react to increased demand and easily expand your deployment.

FortiToken Mobile
FortiToken Mobile is an OATH compliant One-Time Password generator application for the mobile device supporting both time and event based tokens.
Learn More
Identity and Access Management
Identity and Access Management products provide the services necessary to securely confirm the identity of users and devices as they enter the network.
Learn More
